The main utilization examples undertaken by users of StarBED are described below.
| No. | Summary | Keywords | Users | Used nodes |
|---|---|---|---|---|
| 6 | ICT security human resources training event in Hardening Project 2015 | Security, Human Resource Training, Competition | LAC Co., Ltd., Tricorder Co., Ltd., NEC Nexsolutions, Ltd., Japan Computer Emergency Response Team Coordination Center, Asterisk Research, Inc., Internet Initiative Japan Inc. |
Max. 100 (Max. 540 virtual nodes) |
| 5 | Evaluations of storing, distributing, and image processing features for uncompressed 8K ultra high resolution streaming video data | Ultra-high-resolution Video, Streaming Delivery | Kanagawa Institute of Technology, NTT Network Innovation Laboratories, NTT IT CORPORATION |
16 (16 virtual nodes) |
| 4 | <Cloud Computing Competition> Deployment of the test environment for cloud computing technology on StarBED |
Competition, Deployment | Interop 2010 | 552 |
| 3 | <IT-Keys> Deployment of the isolated experience-based environments for network-security exercises |
Human Resource Training | MEXT |
242 |
| 2 | Large-scale/wide-range testing in real-world environments related to R&D for the controlling network-application-type contents | Television Conferencing System Technolog | Panasonic Corporation | 100 |
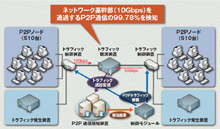
| 1 | Development software to detect 10 gigabit/second, broadband-based P2P-type file-sharing software traffic | Strategic Technology to Prevent the Leaking of Information | Hitachi, Ltd., NEC Corporation |
1,020 virtual nodes |