Utilization Examples
The main utilization examples undertaken by users of StarBED are described below.
- Please refer to: "Research Activity" page
1. Support for MIC* Commissioned Research
<Strategic Technology to Prevent the Leaking of Information**>
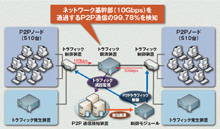
Development software to detect 10 gigabit/second, broadband-based P2P-type file-sharing software traffic |
*: the Ministry of Internal Affairs and Communications (MIC)
**: This content forms part of the results of the "Development of Technology to Detect Information Leaks from Networks and Prevent the Automatic Distribution of Leaked Information" (FY2007-2009) research commissioned by MIC.
- Corporate Users: Hitachi Corporation, NEC (Nippon Electric Company)
- Scale Used: Constructed from a total of 1,020 virtual nodes
- Content of Usage:
The detection experiment was conducted using a total construction of 1,020 P2P nodes and 30 traffic generators within the StarBED facility, and was directed at ISP network housing traced router groups and P2P traffic and similar internet communications, such as e-mail, the web and etc., transmitted worldwide.
2. Support for Research and Development for Private-sector Products
<Television Conferencing System Technology>
| Large-scale/wide-range testing in real-world environments related to R&D for the controlling network-application-type contents |
- Corporate Users: Panasonic Corporation
- Scale Used: 100 nodes
- Content of Usage:
Development of verification methods for a multi-point distribution system using StarBED.
Conducted testing, at the 100 node-scale, on ALM (application layer multicast) function which realizes HD imaging transmission between multiple terminals by duplicating packets and transferring them.
3. Human Resource Training
<IT-Keys Security Human Resource Training>
| We created an isolated experiment environment related to network security and, by using this environment, conducted personal training in coordination with universities etc. so as to verify the functionality and usefulness of the environment used. |
- Scale Used: 242 nodes
- Content of Usage:
We created approximately 20 personal training environments and conducted real-life training on them.

IT-Keys Logo
<Cloud Computing Competition>
| We created a cloud computing technology-testing environment on StarBED and provided this for demonstrations and verification of the cloud computing technology by competition participants. |
- Scale Used: 552 nodes
- Content of Usage:
We created on StarBED a framework and mechanisms for testing cloud computing technology, and allowed the Cloud Computing Competition participants to freely construct cloud computing environments of a scale and complexity close to those in use in real networks.

Logo of Cloud Computing Competition