Making a synthesis emulation in IoT era possible
StarBED4 Project website
Utilization Examples
The main utilization examples undertaken by users of StarBED are described below.
| No. | Summary | Keywords | Users | Used nodes |
|---|---|---|---|---|
| 6 | ICT security human resources training event in Hardening Project 2015 | Security, Human Resource Training, Competition | LAC Co., Ltd., Tricorder Co., Ltd., NEC Nexsolutions, Ltd., Japan Computer Emergency Response Team Coordination Center, Asterisk Research, Inc., Internet Initiative Japan Inc. |
Max. 100 (Max. 540 virtual nodes) |
| 5 | Evaluations of storing, distributing, and image processing features for uncompressed 8K ultra high resolution streaming video data | Ultra-high-resolution Video, Streaming Delivery | Kanagawa Institute of Technology, NTT Network Innovation Laboratories, NTT IT CORPORATION |
16 (16 virtual nodes) |
| 4 | <Cloud Computing Competition> Deployment of the test environment for cloud computing technology on StarBED |
Competition, Deployment | Interop 2010 | 552 |
| 3 | <IT-Keys> Deployment of the isolated experience-based environments for network-security exercises |
Human Resource Training | MEXT |
242 |
| 2 | Large-scale/wide-range testing in real-world environments related to R&D for the controlling network-application-type contents | Television Conferencing System Technolog | Panasonic Corporation | 100 |
| 1 | Development software to detect 10 gigabit/second, broadband-based P2P-type file-sharing software traffic | Strategic Technology to Prevent the Leaking of Information | Hitachi, Ltd., NEC Corporation |
1,020 virtual nodes |
6.ICT security human resources training event in Hardening Project 2015
| Kewords: Security, Human Resource Training, Competition Users: LAC Co., Ltd., Tricorder Co., Ltd., NEC Nexsolutions, Ltd., Japan Computer Emergency Response Team Coordination Center, Asterisk Research, Inc., Internet Initiative Japan Inc. Used nodes: Max. 100 (Max. 540 virtual nodes) |
- Content of Usage:
This human resources training event 'Hardening 10 MarketPlace', which is a security competition, was held at Okinawa on Jun. 20-21, 2015. It was the 6th security event from the 1st event 'Hardening Zero' in Apr. 2012.
The hardening competition events, which aren't a Capture The Flag(CTF), are designed for more practicable technology. In this event, we deployed more than 350 virtual nodes efficiently by using the StarBED facility and our technologies. - Notes:
The 12 teams consisting of 6 competitors per team challenged this event.
They ware given control of a vulnerable EC (electronic commerce) site environment consisting of more than 20 nodes, and competed for sales while responding to attacks. In the competition, they invested in security equipment and services from sales, reported security incidents, and dealt with clients.


Hardening Project Logo
5.Evaluations of storing, distributing, and image processing features for uncompressed 8K ultra high resolution streaming video data
| Kewords: Ultra-high-resolution Video, Streaming Delivery Users: Kanagawa Institute of Technology, NTT Network Innovation Laboratories, NTT IT CORPORATION Used nodes: 16 nodes (16 virtual nodes) |
- Outline:
At the demonstration experiment in Sapporo Snow Festival 2015, the users evaluated the real-time image processing feature and the multipoint distribution switching feature for uncompressed 8K streaming video data by using the StarBED facility.
4.<Cloud Computing Competitio> Deployment of the test environment for cloud computing technology on StarBED
| Kewords: Competition, Deployment Users: Interop 2010 Used nodes: 552 nodes |
- Outline:
We created a cloud-computing test environment on StarBED and provided it as a place to demonstrate and verify the competitors' cloud computing technologies.
In the environment, the competitors freely constructed their own environments whose scale and complexity were close to real networks.

Logo of Cloud Computing Competition
3. <IT-Keys> Deployment of the isolated experience-based environments for network-security exercises
| Kewords: Human Resource Training Users: MEXT Used nodes: 242 nodes |
- Outline:
We created approximately 20 sets of isolated experience-based training environments and verified the functionality and usefulness of them through the training in coordination with universities etc.

IT-Keys Logo
2. Large-scale/wide-range testing in real-world environments related to R&D for the controlling network-application-type contentss
| Kewords: Television Conferencing System Technology Users: Panasonic Corporation Used nodes: 100 nodes |
- Outline:
Development of verification methods for a multi-point distribution system using StarBED.
Conducted testing, at the 100 node-scale, on ALM (application layer multicast) function which realizes HD imaging transmission between multiple terminals by duplicating packets and transferring them.
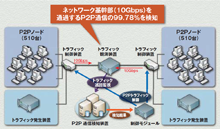
1. Development software to detect 10 gigabit/second, broadband-based P2P-type file-sharing software traffic*
*: This content forms part of the results of the "Development of Technology to Detect Information Leaks from Networks and Prevent the Automatic Distribution of Leaked Information" (FY2007-2009) research commissioned by MIC.
| Kewords: Strategic Technology to Prevent the Leaking of Information Users: Hitachi, Ltd., NEC Corporation Used nodes: 1,020 virtual nodes |
- Outline:
The detection experiment was conducted using a total construction of 1,020 P2P nodes and 30 traffic generators within the StarBED facility, and was directed at ISP network housing traced router groups and P2P traffic and similar internet communications, such as e-mail, the web and etc., transmitted worldwide.